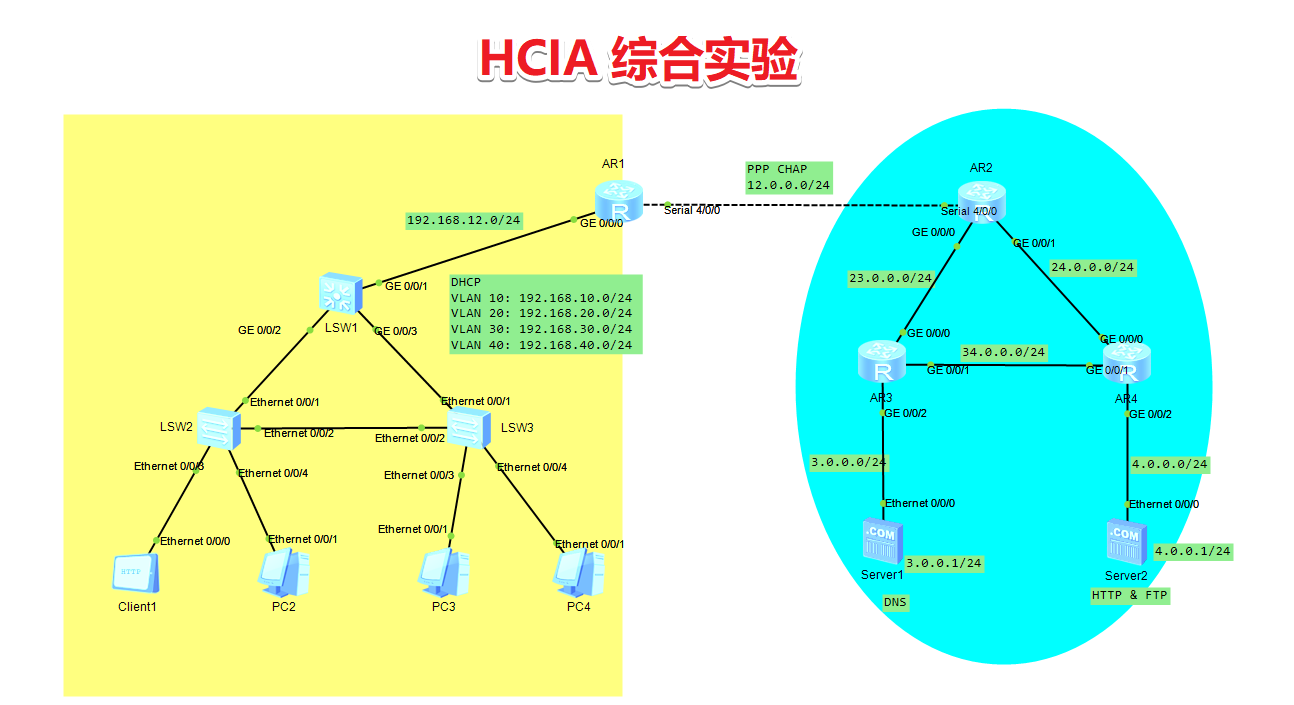
实验要求 【配置说明】
【配置要求】
配置telnet,要求所有网络设备均支持远程管理,密码为000.com 配置Trunk,交换机之间的链路均为Trunk模式 配置VLAN,在SW2和SW3上创建相关VLAN,关联4台PC到对应的VLAN接口 配置MLS,通过SW1实现VLAN间路由 配置DHCP,使SW1成为所有的VLAN的根桥,要求手动修改优先级为4096 配置OSPF,企业内网运行ospf1 配置缺省和NAT,在R1上配置静态缺省路由,SW1通过OSPF学习缺省路由 配置NAT,在R1上配置PAT(只需要转换四个VLAN网段) 配置ppp,R1和R2之间封装协议为ppp,使用CHAP双向认证,密码为111.com 配置OSPF,R2和R3和R4之间运行ospf2 配置DNS,可以通过www.abc.com 访问HTTP服务器,通过www.123.com访问FTP服务器 配置ACL,在R1上配置ACL,拒绝VLAN10的主机通过浏览器访问http服务器,其他流量不受影响 配置过程 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 #SW2 sys sys SW2 user-interface vty 0 4 authentication-mode aaa aaa local-user pengxb password cipher 000.com local-user pengxb privilege level 15 local-user pengxb service-type telnet vlan batch 10 20 30 40 int eth0/0/1 p l t port trunk allow-pass vlan 10 20 30 40 int eth0/0/2 p l t port trunk allow-pass vlan 10 20 30 40 int eth0/0/3 p l a p d vlan 10 int eth0/0/4 p l a p d vlan 20 ##################################################### #SW3 sys sys SW3 user-interface vty 0 4 authentication-mode aaa aaa local-user pengxb password cipher 000.com local-user pengxb privilege level 15 local-user pengxb service-type telnet vlan batch 10 20 30 40 int eth0/0/1 p l t port trunk allow-pass vlan 10 20 30 40 int eth0/0/2 p l t port trunk allow-pass vlan 10 20 30 40 int eth0/0/3 p l a p d vlan 30 int eth0/0/4 p l a p d vlan 40 ##################################################### sys sys SW1 stp priority 4096 dhcp enable user-interface vty 0 4 authentication-mode aaa aaa local-user pengxb password cipher 000.com local-user pengxb privilege level 15 local-user pengxb service-type telnet vlan batch 10 20 30 40 12 int g0/0/1 p l a p d vlan 12 int vlanif12 ip a 192.168.12.1 24 int g0/0/2 p l t port trunk allow-pass vlan 10 20 30 40 int g0/0/3 p l t port trunk allow-pass vlan 10 20 30 40 int vlanif10 ip a 192.168.10.254 24 dhcp select interface dhcp server dns-list 3.0.0.1 int vlanif20 ip a 192.168.20.254 24 dhcp select interface dhcp server dns-list 3.0.0.1 int vlanif30 ip a 192.168.30.254 24 dhcp select interface dhcp server dns-list 3.0.0.1 int vlanif40 ip a 192.168.40.254 24 dhcp select interface dhcp server dns-list 3.0.0.1 ospf 1 router-id 192.168.12.1 area 0 network 192.168.10.0 0.0.0.255 network 192.168.20.0 0.0.0.255 network 192.168.30.0 0.0.0.255 network 192.168.40.0 0.0.0.255 network 192.168.12.1 0.0.0.0 ##################################################### sys sys R1 user-interface vty 0 4 authentication-mode aaa aaa local-user pengxb password cipher 000.com local-user pengxb privilege level 15 local-user pengxb service-type telnet acl 2000 rule 1 permit acl 3000 rule 1 deny tcp source 192.168.10.0 0.0.0.255 destination 4.0.0.1 0 int g0/0/0 ip a 192.168.12.2 24 traffic-filter inbound acl 3000 int s4/0/0 ip a 12.0.0.1 24 ppp chap user ppp ppp chap password cipher 111.com nat outbound 2000 ppp authentication-mode chap ospf 1 router-id 192.168.12.2 area 0 network 192.168.12.2 0.0.0.0 default-route-advertise q ip route-static 0.0.0.0 0 12.0.0.2 ##################################################### sys sys R2 user-interface vty 0 4 authentication-mode aaa aaa local-user pengxb password cipher 000.com local-user pengxb privilege level 15 local-user pengxb service-type telnet local-user ppp password cipher 111.com local-user ppp service-type ppp int s4/0/0 ip a 12.0.0.2 24 int g0/0/0 ip a 23.0.0.1 24 int g0/0/1 ip a 24.0.0.1 24 ospf 2 router-id 23.0.0.1 area 0 network 23.0.0.0 0.0.0.255 network 24.0.0.0 0.0.0.255 network 12.0.0.2 0.0.0.0 ##################################################### sys sys R3 user-interface vty 0 4 authentication-mode aaa aaa local-user pengxb password cipher 000.com local-user pengxb privilege level 15 local-user pengxb service-type telnet int g0/0/0 ip a 23.0.0.2 24 int g0/0/1 ip a 34.0.0.1 24 int g0/0/2 ip a 3.0.0.254 24 ospf 2 router-id 23.0.0.2 area 0 network 23.0.0.0 0.0.0.255 network 34.0.0.0 0.0.0.255 network 3.0.0.0 0.0.0.255 ##################################################### sys sys R4 user-interface vty 0 4 authentication-mode aaa aaa local-user pengxb password cipher 000.com local-user pengxb privilege level 15 local-user pengxb service-type telnet int g0/0/0 ip a 24.0.0.2 24 int g0/0/1 ip a 34.0.0.2 24 int g0/0/2 ip a 4.0.0.254 24 ospf 2 router-id 24.0.0.2 area 0 network 24.0.0.0 0.0.0.255 network 34.0.0.0 0.0.0.255 network 4.0.0.0 0.0.0.255
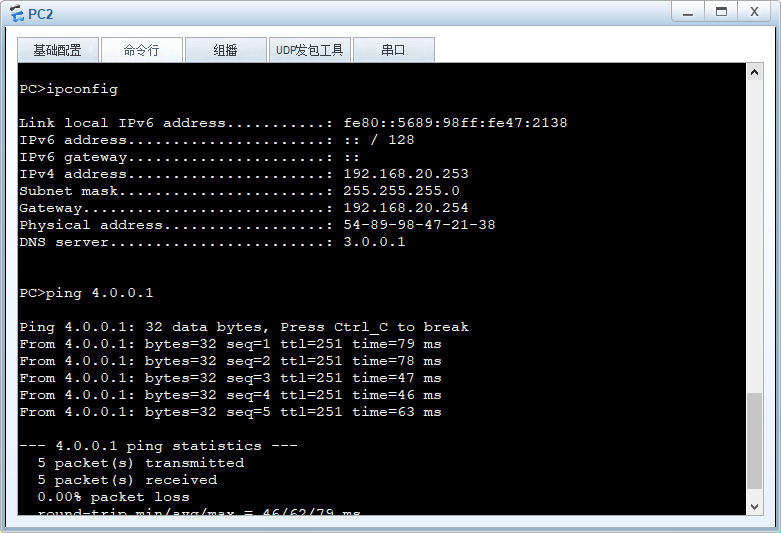
验证配置结果 从pc2 ping 服务器
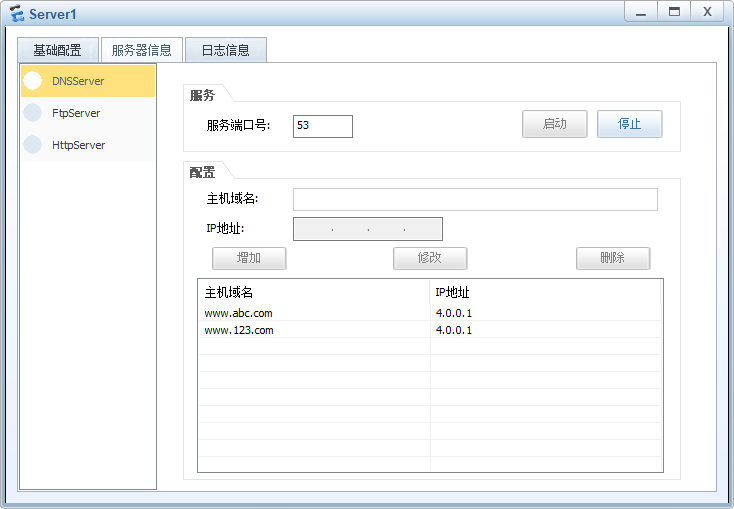
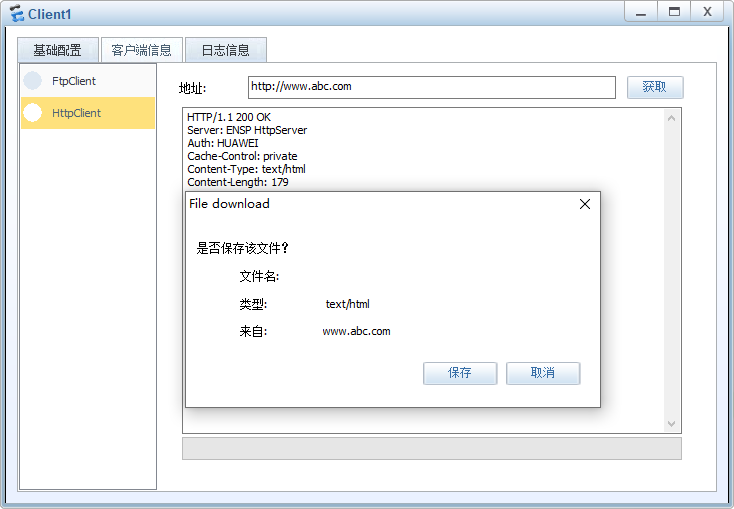
开启dns服务,配置域名解析
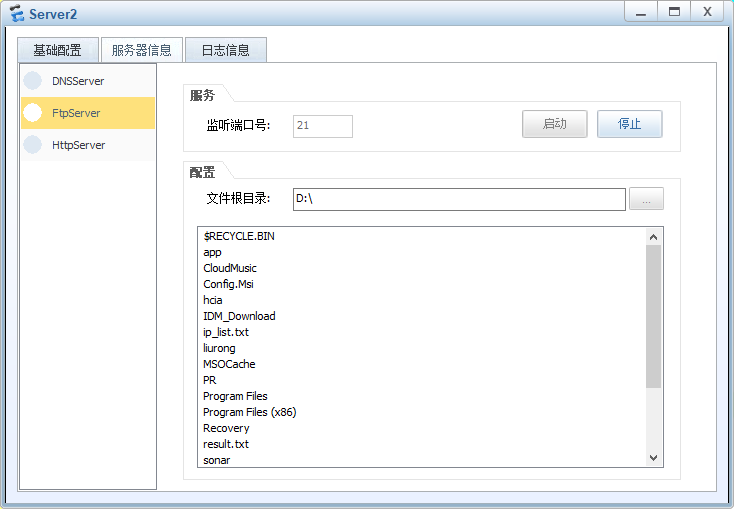
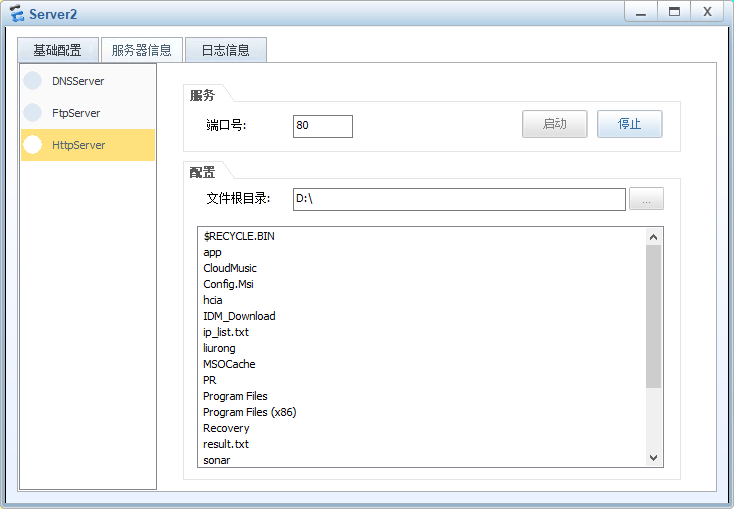
在服务器上开启ftp和http服务
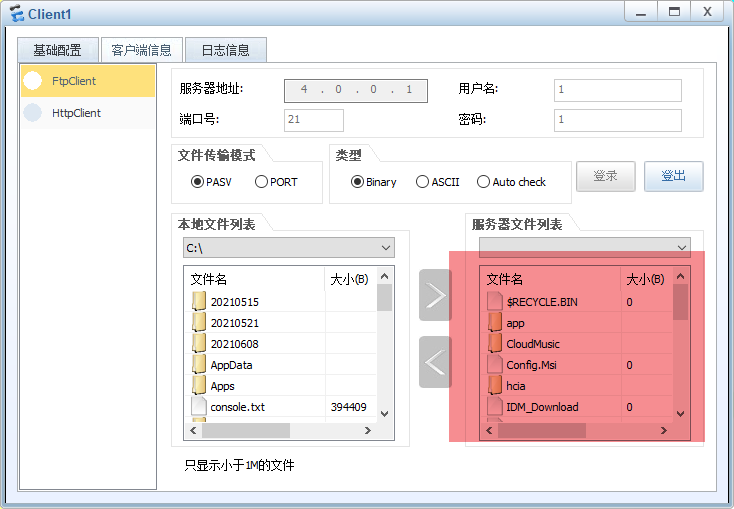
在client1上测试ftp访问
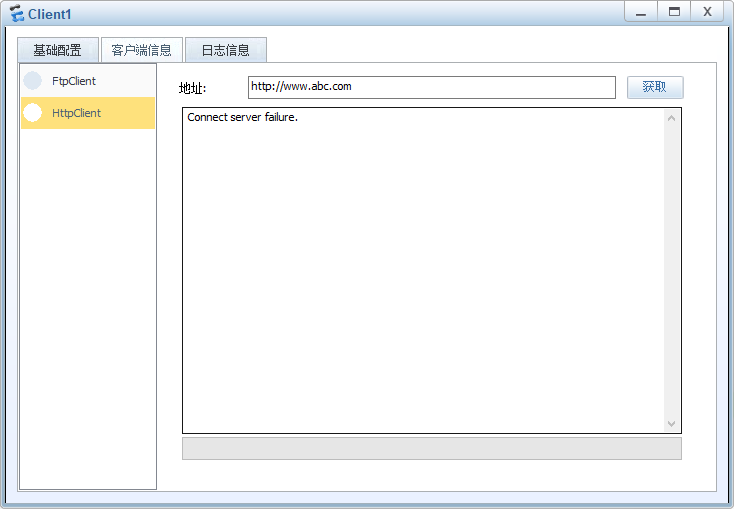
关闭&开启acl过滤,测试
1 2 3 4 5 6 #AR1 int g0/0/0 #关闭acl过滤 undo traffic-filter inbound #开启acl过滤 traffic-filter inbound acl 3000